External Secrets
Specify secret name in PlatformApplication
Edit .platform/kubernetes/base/application.yaml and add your secret names
spec:
secrets:
- name: sample-service
Add external secret resource
Azure KeyVault
- Once your application is deployed,
PlatformApplicationoperator will automatically create Azure Key Vault with admin groups based on CloudConfig and name same as application name. - Add Secrets Manually in KeyVaults
- Click on specified KeyVault -> Objects -> Secrets -> Generate/import
- Set
Nameas your secret namesample-service, setSecret Valueas JSON format like:
{
"KEY_NAME_1": "VALUE_1",
"KEY_NAME_2": "value_2",
"FOO": "BAR"
}
- Verify your
ExternalSecretandSecretis healthy in ArgoCD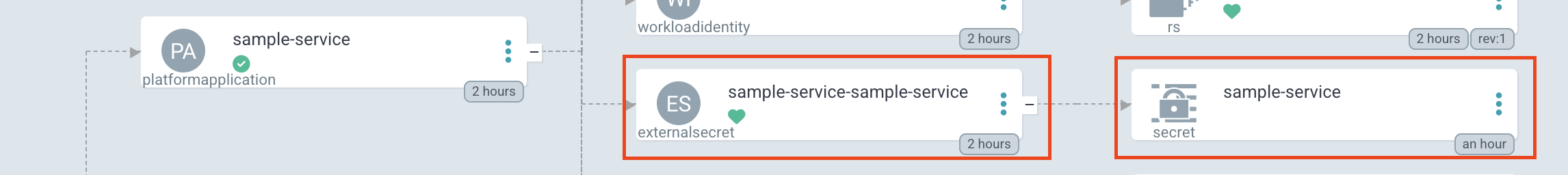
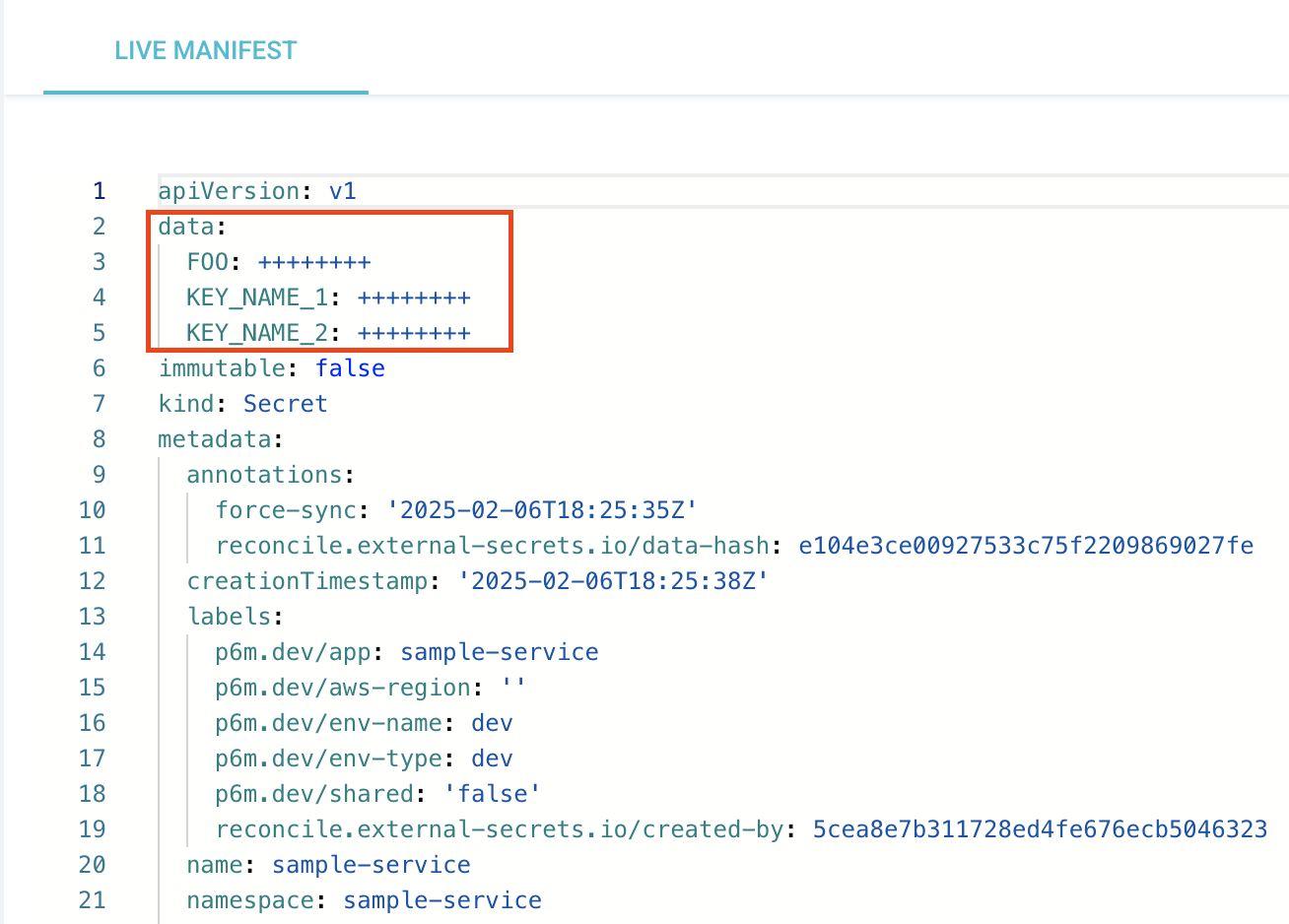
- Restart your Deployment, so these key-value pairs is injected to your pods as Environment Variables
AWS Secret Store
- Go to AWS Secrets Manager in AWS Console
- Click
Store New Secret, SelectOther type of secret, Add key-value pair for your secrets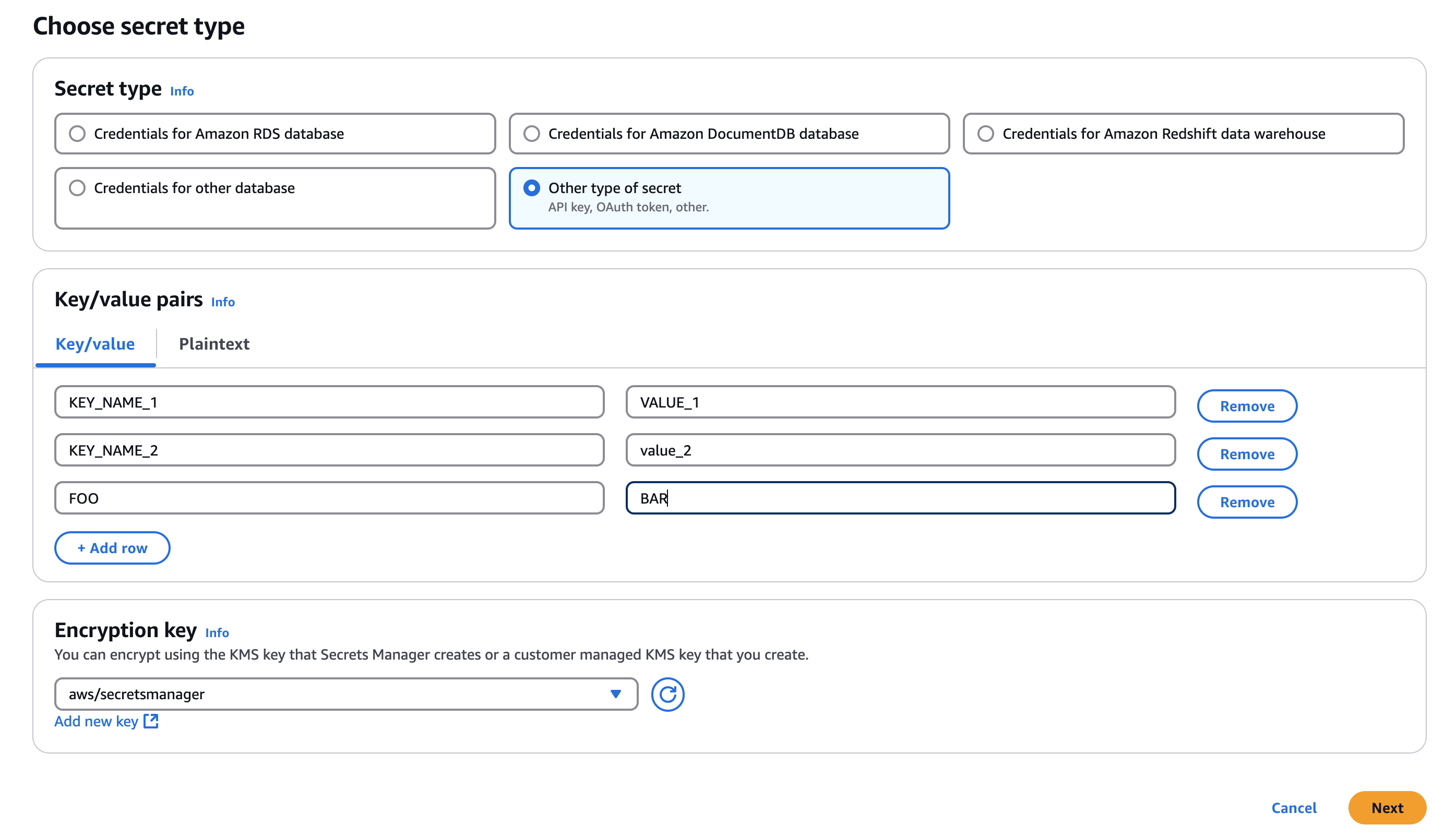 You could also use plain text:
You could also use plain text:
{
"KEY_NAME_1": "VALUE_1",
"KEY_NAME_2": "value_2",
"FOO": "BAR"
}
- Click
Next, Specify secret name it appears in application.yaml assample-service. Save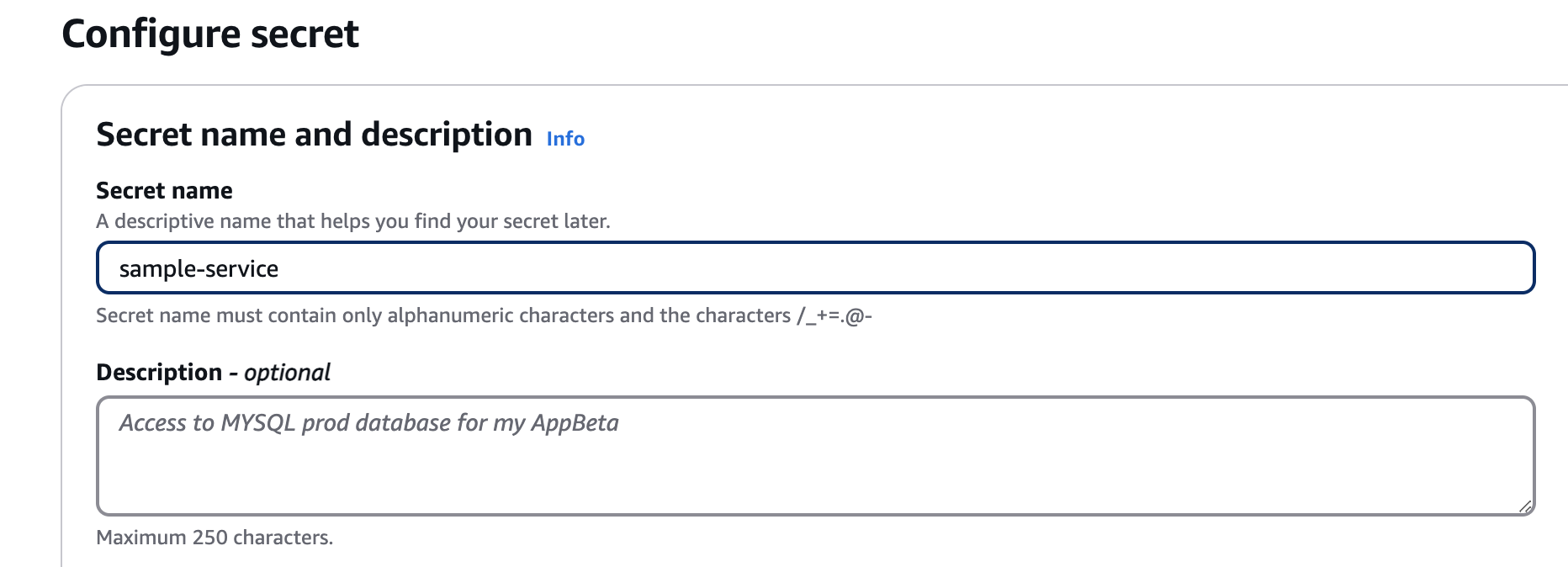
- Verify your
ExternalSecretandSecretis healthy in ArgoCD

- Restart your Deployment, so these key-value pairs is injected to your pods as Environment Variables